Solar inverter cyber security strategy that improves system monitoring

The war in Ukraine is another reminder that cyber security is of utmost importance — and hardening the cyber security of an electric grid with thousands of interconnected DER starts with the inverter. SunSpec Alliance is hosting a great educational series on the topic.
In the recent “DER Cybersecurity – Solar Inverter Risks and Defenses from Power Electronics Hardware Attacks,” Alan Mantooth, distinguished professor of electrical engineering at University of Arkansas, and lead of the UA Power Group, explained his group’s approach to hardening cyber security at the inverter level while also helping to properly manage a distributed grid – all for about an extra $100 per inverter.
“We don’t want the modernization of the electric power grid, which involves more inverter-based generation and DER and digital-based controls to be perceived as causing degradation in the reliability of our electric power grid, but that could be the result if not properly managed and cared for,” Mantooth said during the webinar.
The UA Power Group is working with the Department of Energy’s Solar Energy Technology Office (SETO), to test and develop this concept. Right now they are mimicking a solar farm and deploying their cyber security methods in a mock demo before hitting the field later this year.
What are the risks?
Attacks that hit the hardware level could lead to all sorts of problems down the line.
- Power quality issues
- Damage to the battery energy storage (could result in fires)
- Damage to switchgear (switching on and off rapidly)
- Damage to downstream equipment
- Lack of performance and lack of resiliency.
Under connected scenarios, attacks can come from the communications portal. These are “man in the middle” attacks, such as intercepting data and commands and making things seem normal but they’ve taken control. Denial of service is another, flooding the system with info and preventing you from having real-time awareness of what’s happening.
Under unconnected scenarios, the attacks can come from insider threats or access via USB ports. Plug that thing in and they are in.
“If there’s any way of updating a system, there’s a way in which things can get in,” Mantooth says.
Often, performance issues aren’t from an attack at all. Faulty code or poor choices can have the same implications for how a system is operating. Mantooth has heard at least one utility say this has happened — a patch was deployed in a PV solar system that affected the inverters, resulted in poor power quality, and it took them 60 days to figure out why.
How do we account for all of this?
Our focus here is on a DER hardware solution developed by the UA Power Group, its Universal Controller Board (UCB), which is used for all sorts of things from hybrid bulldozers to hybrid electric aircraft and other grid connected devices.
“At the hardware level, there’s a logic we can add to power electronic designs that prevent the ‘shoot throughs’ from ever being allowed,” Mantooth says, explaining in way more technical detail than I could grasp as to how they can set rules that cannot be violated. “Then the hardware itself will override any control system that tries to do that.”
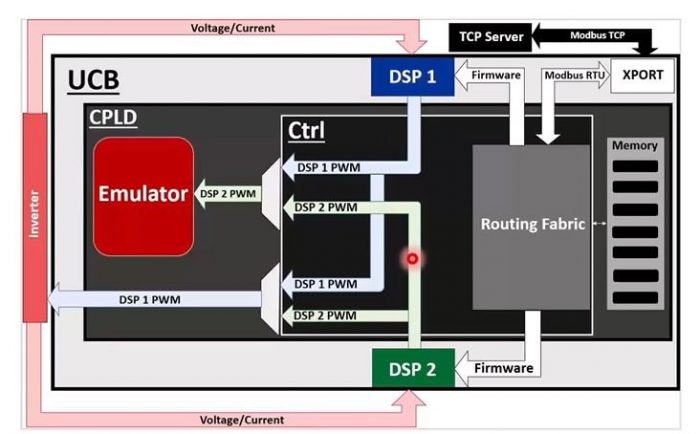
Key to it all is the UCB’s two demand-side platforms (DSPs) and an embedded real-time emulator that, essentially, work constantly to run checks and balances on the system’s performance. One DSP is in control, while the other sits as a real-time digital twin that is controlling an emulator. The DSP not in control does not affect the operations of the system.
“It gets all the same commands and is seeing all the same inputs, but the DSP 1 controls the inverter, while the DSP 2 controls a virtual inverter with all the same loading characteristics — it is running a model of the system in real time,” Mantooth explains. That emulator has a code to show how the system is going to react.
- The embedded digital twin is running real-time in the controller itself to identify if something running does not make sense.
- There’s also a behavioral analysis of new firmware to assess whether an update is truly something that should be deployed based on performance.
System operators can then see what’s happening in the emulator before any firmware or patch is ever deployed. If there is a power quality issue, you have a chance to catch it.
“You can now imagine that I can upload a set of regression tests that this thing needs to pass, inside the emulator, and there is a pass-fail criteria,” Mantooth says. “They can be somewhat autonomous in that regard. I run it through these regressions just to see if anything that failed before is violated again in this new patch. I can catch that in the emulator without having a human go in and look.”
If everything checks out, in a nanosecond, the inverter controls can be switched over from DSP 1 to DSP 2. The emulator is accessed via a web server with two factor authentication and other encryption.
If somehow something nefarious is uploaded upstream and works its way past the emulator …
“If we don’t catch it, we have a DSP and memory on board to go to a safe mode of operation,” he notes. “We can roll back multiple versions to previous known goods, deeper than one back.”
Summary of benefits
- Firmware updates – zero-day attack mitigations and performance enhancements
- Firmware validation – error and threat detection, mitigate insider threats, real-time digital twin
- Reduced downtime – no downtime required for updates, switch DSP control in less than a nanaosecond
- Ability to mitigate problems operators aren’t aware of.
- Real-time anomaly detection.
Other benefits
Scheduled roll outs. Zooming out, there can be blockchain communication at the system level, linking inverter-to-inverter communication for an extra layer of resilience. Say you have a solar farm with 25 inverters…
“The blockchain communicates with the resilient controls, and it becomes one of the nodes in the network. … We can roll out a patch in four or five [inverters], which are participating in a blockchain algorithm to determine if it’s working. And then when we roll it out fully, they are all participating in any anomaly detection.”
Aging system monitoring. Aside from cyber incidents, think about how the emulator can be used to monitor the aging and failure modes of equipment. This setup can monitor how things are naturally degrading and “we have diagnostic capabilities at the hardware level that can be fed back to the twin.”
If you have read this far and are interested, be sure to watch the entire presentation, which goes into a much greater depth.


Comments are closed here.