Report: Nearly 50% of global solar power exposed to cyber exploitation
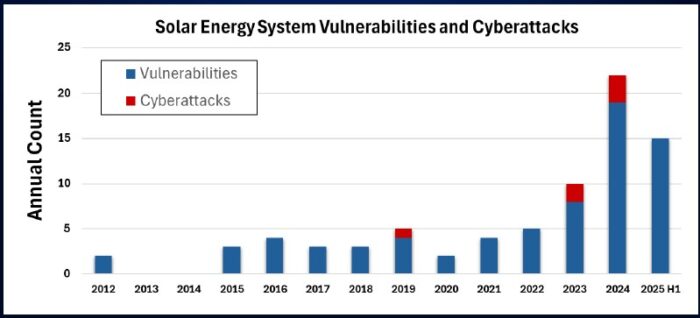
Solar vulnerability disclosures are increasing at an “alarming rate,” according to a report from DER Security Corp (DERSec). By their calculation, approximately ~45% of the world-wide solar generation (>1 TW) is currently exposed to “cyber exploitation.”
DERSec’s first report in November 2024 identified 79 Common Vulnerabilities and Exposures (CVEs) and other issues identified in solar energy cloud software. In an update published this week, DERSec cataloged an additional 50 CVE vulnerabilities in solar-based Distributed Energy Resource (DER) systems.
Who is DERSec
DER Security Corp provides a cyber-physical anomaly detection system that protects against cyberattacks at the device, local network, and cloud levels by correlating the electrical behavior of protected assets with network control signals and out-of-band data streams. The team is comprised of veterans in this space. CEO Tom Tansy was previously the leader at SunSpec and is now board chairman, and CTO Jay Johnson is a former threat hunter from Sandia Labs, who was instrumental in developing U.S. national cybersecurity policies for distributed energy.
What solar systems have vulnerabilities
Solar energy cybersecurity vulnerability disclosures have increased over recent years, with security gaps identified in fielded devices and cloud-based management systems. Vulnerable APIs have exposed more than 1 TW of distributed energy systems to remote control.
Proof-of-concept malicious firmware exploits have demonstrated physical impacts to inverter hardware and upstream protection equipment. Chaining vulnerabilities could lead to extended power systems impacts.
Cyberattacks on solar systems have not garnered significant attention, but the DERSec team says, given the severity and prevalence of vulnerabilities in the solar ecosystem, there is a “substantial risk of sustained, grid-impacting attacks.” They are advocating for stronger security measures in the U.S. that protect solar generators, energy management systems, and electricity grids.
“The recent power outage in the Iberian Peninsula, which has not been confirmed as cyber related, has caused Spanish regulators to investigate the possibility of cyber compromise,” said Tansy. “Spain has 54,000 grid-connected solar installations that supply 70% of the nation’s power. About 50% of the inverters installed in Spain come from vendors named in the report.”
You can download the latest “Public History of Cyberattacks and Vulnerabilities” report here for a complete list of the CVEs they have identified.
Solar power vulnerabilities
DERSec found 129 unique Common Vulnerabilities and Exposures (CVEs) and other issues identified in solar energy cloud software. Most issues were related to solar monitoring systems and gateways, with cloud infrastructure and inverters also having a sizable share of the vulnerabilities.
“From a risk perspective, cloud vulnerabilities would likely lead to more significant impacts because they allow attackers to control gigawatts of generation,” Jay Johnson writes in the report.
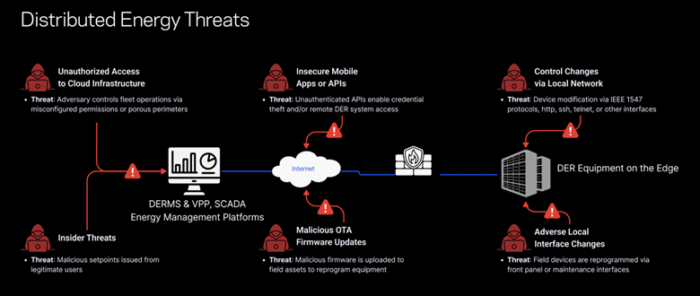
“Because modern solar inverters are a combination of computing devices and power conversion equipment, large-scale impacts on the grid are possible if (a) vendor, operator, or aggregator cloud systems are compromised or (b) valid firmware updates are issued that disable equipment. Negative impacts can be realized with traditional cloud breaches or when attackers gain a foothold on fielded equipment and pivot upstream.”
Scale of the problem
In assessing recent demonstrations of vulnerabilities, Johnson says: “It is not difficult to imagine attacks in which 100s of GWs of solar generation are simultaneously disconnected, sub-synchronous power oscillations are injected, power quality is intentionally degraded with high harmonic distortion, or all power stage switches are closed to short the DER phases and trip protection equipment.
“Worse, given increasing deployment of residential and light commercial battery and hybrid generation systems, additional attack scenarios are plausible outside of typical solar energy generation windows by leveraging bidirectional power flows to exceed distribution or transmission line ratings or overload transformer capacities.”
DERSec recommendations
Cyber regulation in the U.S. only applies to the absolute largest solar installations with NERC CIP compliance mandates, Johnson says.
“Instead of actively addressing small system vulnerabilities, including those highlighted in this paper, the country has pushed voluntary standards/guides, labelling programs, and equipment certifications to fill a massive gap.
“As a result, we now have a frightening prevalence of internet-connected solar systems with default passwords and other weak security practices—often directly controlled by foreign entities that escape scrutiny or formal regulation.
“Given growing PV penetration and a corresponding increase in vulnerabilities, the solar industry needs to adopt stronger security protections for solar systems to prevent substantial attacks on the world’s power systems. We encourage manufacturers and operators of battery energy storage systems, electric vehicle charging systems and building energy management systems to reinforce their networks for the same reason.”
You can download the latest “Public History of Cyberattacks and Vulnerabilities” report here for a complete list of the CVEs they have identified.





Comments are closed here.